mirror of
https://github.com/adulau/MalwareClassifier.git
synced 2024-12-22 08:46:04 +00:00
Clarification of tshark usage
This commit is contained in:
parent
411e39b501
commit
3a5ac67b8b
1 changed files with 7 additions and 1 deletions
|
|
@ -32,6 +32,12 @@ cd capture
|
||||||
ls -1 . | parallel --gnu "cat {1} | tshark -E header=yes -E separator=, -Tfields -e http.server -r {1} | python ./bin/import.py -f {1} "
|
ls -1 . | parallel --gnu "cat {1} | tshark -E header=yes -E separator=, -Tfields -e http.server -r {1} | python ./bin/import.py -f {1} "
|
||||||
```
|
```
|
||||||
|
|
||||||
|
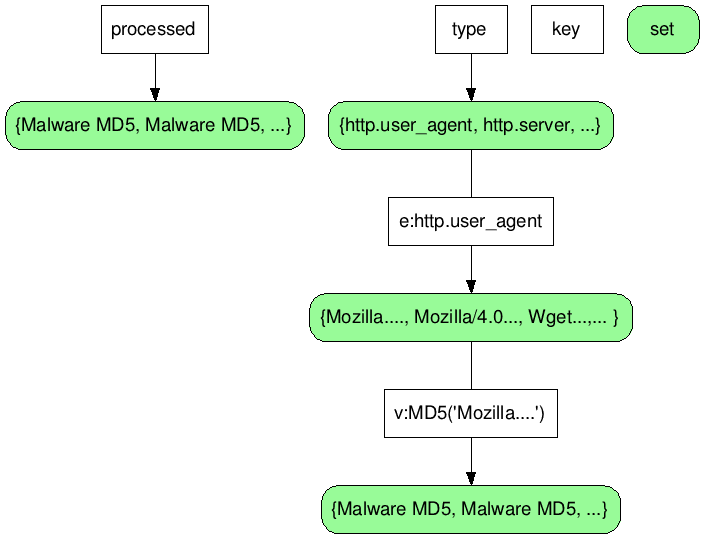
You can add additional attributes like any fields from the dissectors available within tshark (tshark -G fields). You can add additional fields in the command above. This will update the redis data structure. Then when you have enough attributes, you can dump a graph out of the relationships between the attributes and the malware packet captures.
|
||||||
|
|
||||||
|
```shell
|
||||||
|
python ./bin/graph.py
|
||||||
|
```
|
||||||
|
|
||||||
## Redis data structure
|
## Redis data structure
|
||||||
|
|
||||||
|

|
||||||
|
|
|
||||||
Loading…
Reference in a new issue